Jacen's Blog
Blatant Cheating - The TTY-Only Challenge Part 3
October 16, 2025
One problem with my TTY-only setup is that I don't have a way to link it into my blog workflow. That means that chronicling my adventures from within the TTY isn't possible yet. Today, I'm going to fix that by blatantly cheating.
Read more...
The Nintendo DS But Better? - MagicX Zero 40 Review
August 18, 2025
I've mentioned before that I'm a fan of the DS family of handhelds. So, when I heard about the MagicX Zero 40, a handheld purpose-built for DS emulation, I was immediately intrigued. Is it something that can replace my daily-driver 2DS XL? Let's dive into it.
Read more...
TryHackMe - The Marketplace
August 17, 2025
The Marketplace is a medium-ranked box on TryHackMe. It contains a variety of interesting steps along the killchain. While it isn't super difficult, it does take some critical thinking and good enumeration to get through.
Read more...
Staying Entertained - The TTY-Only Challenge Part 2
August 15, 2025
In the first post in this series, we set up a TTY-only laptop running Arch Linux with the intent of daily driving it. We got a lot of the productivity essentials done, but we didn't do much in the way of entertainment. Let's start looking into how we can make things less boring and have fun in our command-line environment.
Read more...
TryHackMe - Git Happens
August 5, 2025
Git Happens is an easy-ranked box on TryHackMe. It's extremely short and simple, but it serves as a good reminder of the dangers of using Git if you don't really know what you're doing.
Read more...
Can You Use Linux Without Leaving The Command Line? - The TTY-Only Challenge
August 2, 2025
One of the most parroted advantages of Linux is its customizability. With plenty of distributions, desktop environments, window managers, and many combinations thereof, there are so many ways to tune your graphical environment exactly the way you want it.
So, what if we take all of that away and strip Linux down to its core? Can we use Linux from just the command line the way people did back in the early days of computing? There's only one way to find out, and that's to try it for ourselves.
Read more...
The Whole-Home AdGuard Proxy
July 14, 2025
I've talked about adblockers in the past, particularly my dislike of Pi-hole and preference toward AdGuard. However, AdGuard comes with a number of hangups, namely that you need a license for every device in your home that you want to protect. But what if you could protect your entire home from a single server? Is it doable?
Read more...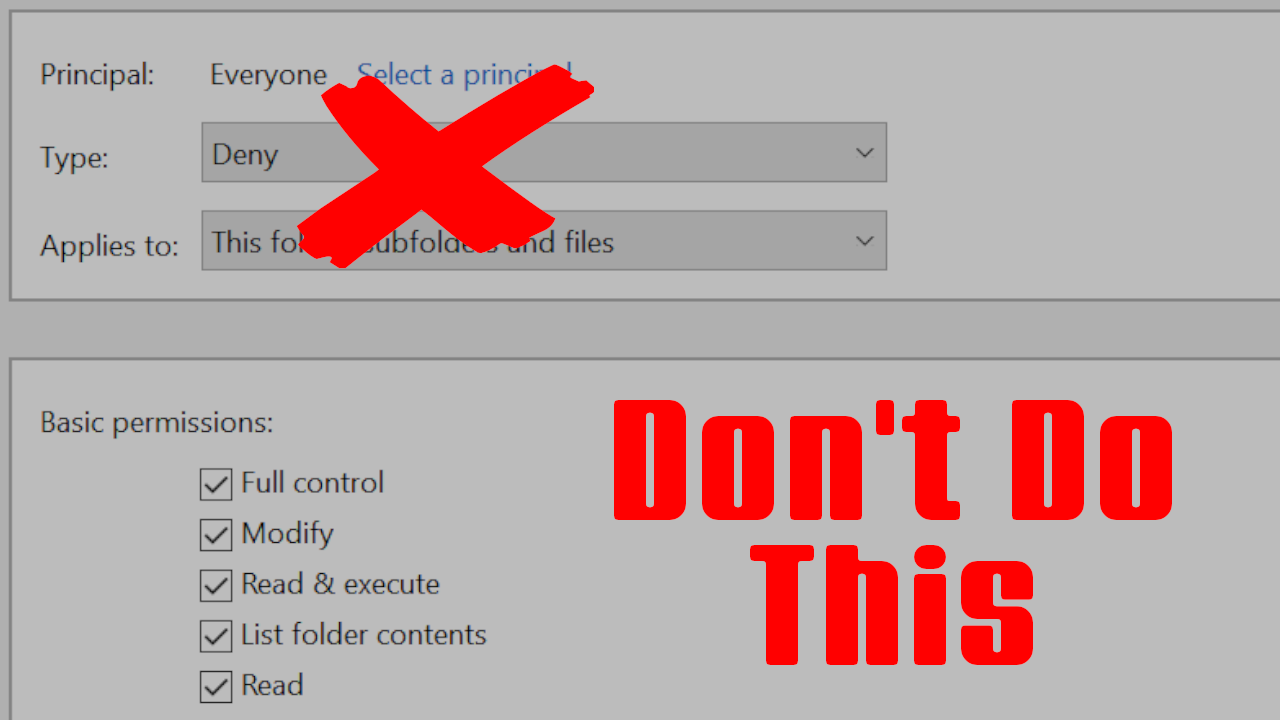
IT Pro Tip - Don't Deny Permissions
July 12, 2025
You're setting up a new shared folder on a Windows file server, probably one that holds sensitive information. You want to be sure that no one unauthorized can access the files, so in the Security tab, you set a new permission entry to deny access to the "Everyone" object.
You've just fallen for one of the oldest pitfalls in the book. Let's go over Windows file permissions and why the "deny" permission is one of the most dangerous.
Read more...
IT Pro Tip - Recovering Local Admin Access
June 21, 2025
Even in a domain environment, once in a while things go wrong and you need a local administrator account. Maybe you're taking over for an unhelpful rival IT department, or maybe you've had an employee who didn't document things correctly. Regardless of the reason, sometimes you just don't have access to everything you need to do your job.
Read more...
The GL.iNet Comet - A Review
May 3, 2025
A while back, I purchased GL.iNet's AC1300 router for a project that never ended up materializing. Despite that, it is still a staple in my backpack, and it put GL.iNet on my radar. So, when I received an email about the GL-RM1 Comet remote KVM, my interest was definitely piqued.
Read more...